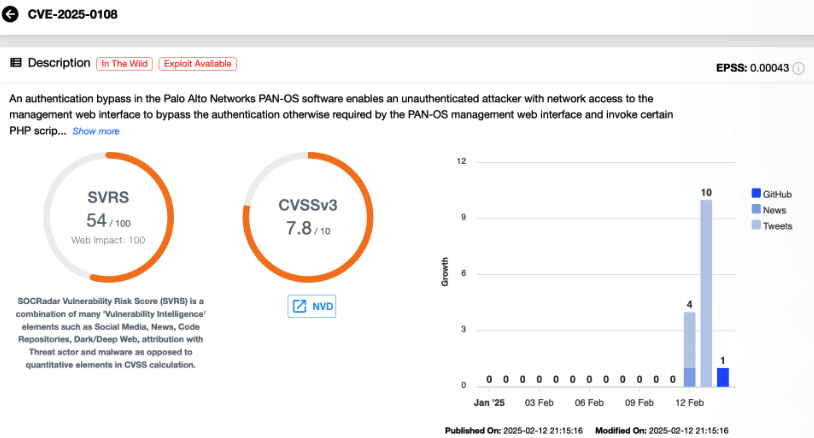
CVE-2025-0108
Palo Alto Networks Authentication Bypass Vulnerability

DESCRIPTION
CVE-2025-0108 is an authentication bypass vulnerability affecting Palo Alto Networks’ PAN-OS management web interface. This flaw allows unauthenticated attackers with network access to the management interface to bypass authentication and invoke certain PHP scripts. While it does not enable remote code execution (RCE), it poses significant risks to system integrity and confidentiality.
The vulnerability stems from path confusion in how Nginx and Apache process authentication requests. Nginx acts as a reverse proxy, setting the X-pan-AuthCheck header for authentication. However, due to inconsistencies in URL handling between Nginx and Apache, attackers can manipulate encoded URLs to bypass authentication checks.
Security researchers have detected active exploitation attempts in the wild, making it critical for organizations to apply patches and reinforce security immediately.
AFFECTED SYSTEMS
The following PAN-OS versions are vulnerable to CVE-2025-0108:
• PAN-OS 11.2 – Versions earlier than 11.2.4-h4
• PAN-OS 11.1 – Versions earlier than 11.1.6-h1
• PAN-OS 10.2 – Versions earlier than 10.2.13-h3
• PAN-OS 10.1 – Versions earlier than 10.1.14-h9
Organizations using these versions should immediately assess their exposure and apply the recommended security patches.
VULNERABILITY IMPACT
• Authentication Bypass: Allows attackers to bypass login authentication for the PAN-OS management web interface.
• Unauthorized Access to PHP Scripts: Attackers can invoke specific PHP scripts, potentially compromising system integrity.
• Risk to Data Confidentiality & Integrity: While not leading to full RCE, this flaw enables unauthorized access to sensitive firewall configurations and logs.
• Active Exploitation in the Wild: Attackers are already probing and attempting to exploit this vulnerability, increasing the risk of real-world attacks.
Technical Details of the Exploit
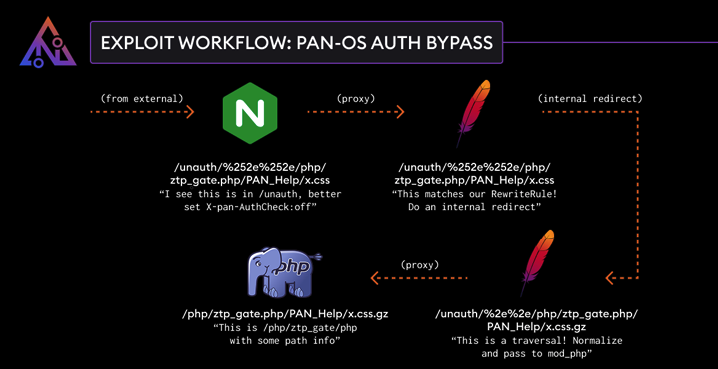
Step 1: Nginx Misinterpretation – A crafted request containing a double-encoded URL (e.g., /unauth/%252e%252e/php/ztp_gate.php/PAN_help/x.css) tricks Nginx into marking it as unauthenticated.
Step 2: Apache Decoding – Apache processes the same request, decoding it again and applying an internal redirect that normalizes the path.
Step 3: Authentication Bypass – Since Nginx had already set the authentication flag off, the request proceeds without authentication, allowing access to restricted PHP scripts.
RECOMMENDATIONS
Immediate Actions:
1. Apply Security Patches – Upgrade PAN-OS to the latest patched versions:
• PAN-OS 11.2.4-h4 and later
• PAN-OS 11.1.6-h1 and later
• PAN-OS 10.2.13-h3 and later
• PAN-OS 10.1.14-h9 and later
2. Restrict Access to the Management Interface
• Ensure firewall management interfaces are not publicly accessible.
• Use jump boxes or VPNs to control and restrict access.
3. Monitor Logs for Suspicious Activity
• Analyze network logs for unusual authentication attempts or requests targeting PHP scripts.
• Use SIEM solutions to detect exploitation attempts.
Long-Term Mitigations
• Enable Multi-Factor Authentication (MFA): Adds an extra layer of security for administrative access.
• Review Past Security Advisories: Ensure no misconfigurations exist that could expose the firewall to similar vulnerabilities.
• Conduct Regular Security Audits: Periodically assess firewall configurations and access controls.
By taking immediate action to apply patches and strengthen security controls, organizations can mitigate the risks posed by CVE-2025-0108.