CVE-2025-21298
Windows OLE Remote Code Execution Vulnerability

DESCRIPTION
CVE-2025-21298 is a critical vulnerability in Windows Object Linking and Embedding (OLE) technology, allowing remote code execution (RCE) via Microsoft Outlook. Attackers can exploit the flaw by sending a specially crafted email containing malicious OLE objects. If the email is opened or previewed in Outlook, the malicious OLE object executes, requiring no additional user interaction. This makes the vulnerability particularly dangerous, as it enables attackers to gain control over affected systems easily. The issue has a CVSS score of 9.8, highlighting its severe risk.
AFFECTED SYSTEMS
The vulnerability impacts the following systems
Microsoft Outlook versions:
• Outlook for Microsoft 365
• Outlook 2024
• Outlook 2021
• Outlook 2019
• Outlook 2016
• Outlook 2013
VULNERABILITY IMPACT
• Remote Code Execution (RCE): Attackers can execute arbitrary code with user-level or administrative privileges.
• Potential Full System Compromise: Exploitation can lead to malware installation, creation of backdoors, and unauthorized access to sensitive information.
• No User Interaction Required: The exploit can trigger by simply previewing a malicious email in Outlook.
• Significant Impact on Email Security: Enterprises relying on Outlook for communication are at high risk.
RECOMMENDATIONS
Immediate Actions:
1. Apply the Latest Patch: Update to the patched version of Outlook provided in Microsoft’s 2025 Patch Tuesday update.
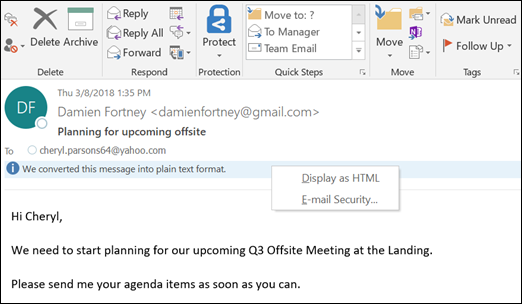
2. Read Emails in Plain Text Format, Steps:
• Open Outlook and click the File tab.
• Select Options > Trust Center > Trust Center Settings > Email Security.
• Check the box Read all standard mail in plain text.
Impact: Rich content, such as images and specialized fonts, will not display, and animations may not work.
3. Avoid RTF Attachments from Untrusted Sources: Be cautious of emails containing Rich Text Format (RTF) content or attachments from unknown senders.
4. Principle of Least Privilege: Restrict user permissions to minimize the impact of successful exploitation.
Note: If you want to view a plain text message in its original format, click the InfoBar, and choose Display as HTML.
Long-Term Mitigations:
• Enable Advanced Threat Protection: Use security tools and policies that can identify and block suspicious emails before they reach users.
• Monitor Network Traffic: Regularly analyze system logs and network activity for signs of exploitation attempts.
• Educate Employees: Conduct training sessions on identifying phishing and malicious email content.