Cloudflare Breach Exploiting Credentials Used Stolen Okta
Cloudflare revealed that a suspected nation-state actor used stolen Okta credentials from a Thanksgiving Day attack to breach Cloudflare's systems in late November.

In a statement released by Cloudflare, the company disclosed that in late November, their systems were breached by a suspected nation-state actor who utilized stolen Okta credentials from a Thanksgiving Day attack. According to Cloudflare, the attack was detected on Thanksgiving Day when the company's security team discovered a threat actor on their self-hosted Atlassian server.
Cloudflare's CEO, Matthew Prince, and others immediately initiated an investigation and cut off the threat actor's access. On November 26, they brought in CrowdStrike's Forensic team for an independent analysis. The CrowdStrike investigation revealed that the threat actor conducted reconnaissance from November 14 to 17 and accessed several internal systems, including their internal wiki and bug database.
On November 20 and 21, the threat actor returned and gained access to Cloudflare's source code management system. The actor also attempted to access other systems using access tokens and service account credentials stolen during the widely-publicized October breach at Okta.
Although the operational impact of the incident was believed to be extremely limited, Cloudflare took the incident seriously as the threat actor used stolen credentials to access their Atlassian server and accessed some documentation and a limited amount of source code.
Below are the Indications of Compromise (IOCs) that we saw from this threat actor. We are publishing them so that other organizations, and especially those that may have been impacted by the Okta breach, can search their logs to confirm the same threat actor did not access their systems.
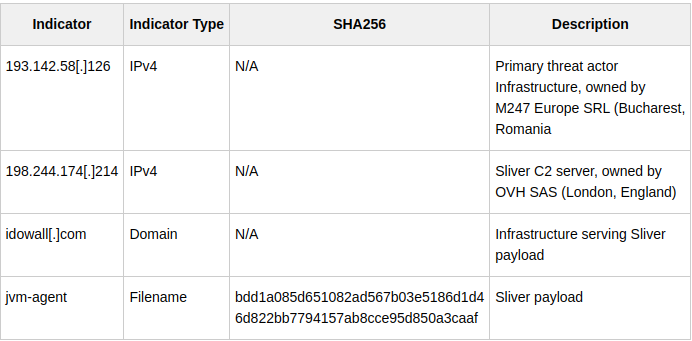
To ensure the threat actors did not have persistent access to other systems, Cloudflare took extensive preventive measures. They rotated every production credential — approximately 5,000 credentials — and physically segmented test and staging systems to prevent the threat actor from using technical information about their network operations as a means to re-enter.
Cloudflare also replaced hardware used in a data center in São Paulo that the threat actor attempted to access. Although no Cloudflare customer data was impacted, Cloudflare took the incident seriously and took necessary preventive actions to secure their network.
Additionally, Cloudflare expressed concerns about Okta's handling of security incidents. They highlighted that this was the second time they were impacted by a breach of Okta's systems. In October, Cloudflare disclosed that the attack was carried out using compromised authentication tokens at Okta, but no Cloudflare customer data was affected. Nevertheless, Cloudflare emphasized the importance of timely security incident disclosure and expressed concerns about Okta's handling of security incidents.
In conclusion, while Cloudflare successfully mitigated the impact of the attack and strengthened their network security, the incident underscores the evolving threat of cybersecurity and the importance for companies to fortify their defenses and enhance cooperation in combating cyber threats.