CVE-2023-42788
FortiManager / FortiAnalyzer OS command injection

DESCRIPTION
CCVE-2023-42788 is a security vulnerability affecting Fortinet FortiManager and FortiAnalyzer software. This vulnerability falls under the category of "OS Command Injection," which refers to issues where software fails to properly process specific elements in operating system (OS) commands, enabling a local attacker with low privileges to execute unauthorized code through specially crafted arguments in command-line interface (CLI) commands.
The vulnerability occurs when FortiManager and FortiAnalyzer software construct all or part of an operating system command using affected input from an upstream component, and the software fails to properly process or sanitize special elements that could alter the intended operating system command when passed to a downstream component.
This vulnerability has been rated high with a score of 7.8 according to the Common Vulnerability Scoring System (CVSS) version 3. This classification indicates that the vulnerability has serious potential for exploitation.
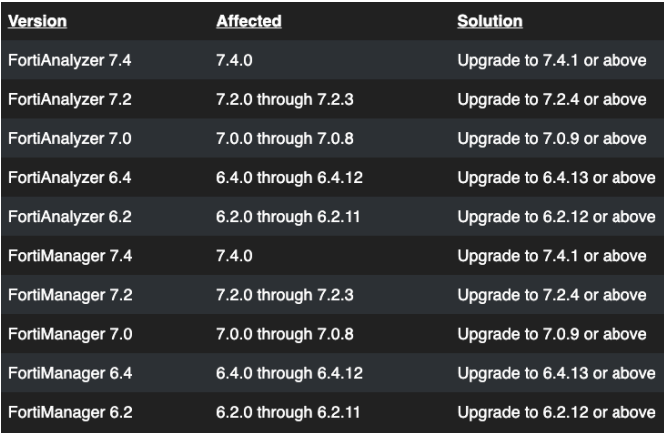
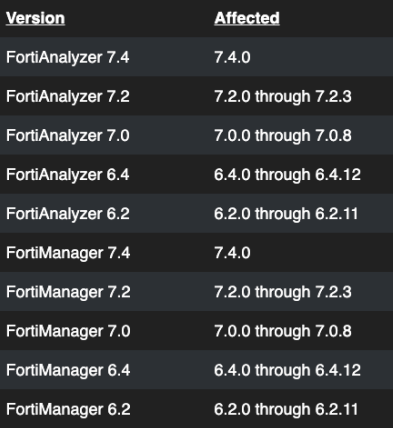
AFFECTED SYSTEMS
VULNERABILITY IMPACT
The impact of CVE-2023-42788 vulnerability affecting Fortinet FortiManager and FortiAnalyzer can be highly severe. The "OS Command Injection" type vulnerability essentially allows attackers with low or restricted privileges to execute unauthorized operating system commands on the vulnerable device. The impact of this vulnerability includes:
• Unauthorized Code Execution: Attackers who successfully exploit this vulnerability can execute unauthorized commands or code on the affected device. This could include running malicious scripts or operating system commands that can cause damage or take over the device.
• Potential Unauthorized Access: By executing unauthorized commands, attackers can gain unauthorized access to the affected system. This could include access to sensitive data, system configurations, or even control over the affected device.
• Potential for Further Intrusion: If attackers gain unauthorized access, they can use this as a foothold to launch further attacks within the network or affected systems, leading to further damage.
RECOMMENDATIONS
The information provided in the CVE-2023-42788 description pertains to affected versions of Fortinet FortiManager or FortiAnalyzer software. In such situations, it is crucial to contact the software provider, Fortinet, for details regarding the impacted versions and updated versions to mitigate this attack.